
Introduction to Access Control
The purpose of access control is to grant entrance to a building or office only to those who are authorized to be there. The deadbolt lock, along with its matching brass key, was the gold standard of access control for many years; however, modern businesses want more. Yes, they want to control who passes through their doors, but they also want a way to monitor and manage access. Keys have now passed the baton to computer-based electronic access control systems that provide quick, convenient access to authorized persons while denying access to unauthorized ones.
What is Access control and how is works?
Access control is a security technique that regulates who or what can view or use resources in a computing environment. It is a fundamental concept in security that minimizes risk to the business or organization.
There are two types of access control: physical and logical. Physical access control limits access to campuses, buildings, rooms and physical IT assets. Logical access control limits connections to computer networks, system files and data.
To secure a facility, organizations use electronic access control systems that rely on user credentials, access card readers, auditing and reports to track employee access to restricted business locations and proprietary areas, such as data centers. Some of these systems incorporate access control panels to restrict entry to rooms and buildings as well as alarms and lockdown capabilities to prevent unauthorized access or operations.
Access control systems perform identification authentication and authorization of users and entities by evaluating required login credentials that can include passwords, personal identification numbers (PINs), biometric scans, security tokens or other authentication factors. Multifactor authentication, which requires two or more authentication factors, is often an important part of layered defense to protect access control systems.
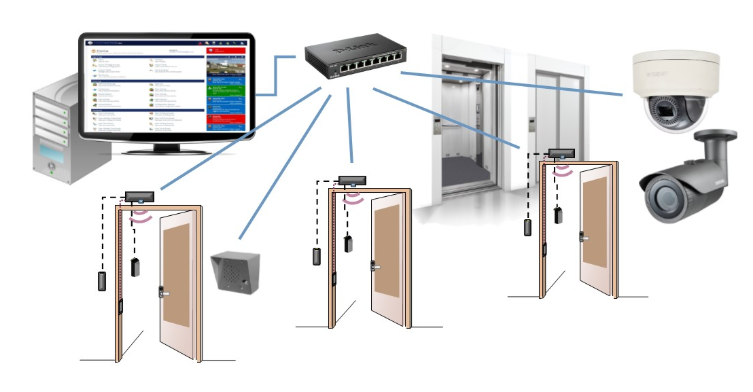
Today, instead of keys, we carry access cards or ID badges to gain entry to secured areas. Access control systems can also be used to restrict access to workstations, file rooms housing sensitive data, printers, as well as entry doors. In larger buildings, exterior door access is usually managed by a landlord, or management agency, while interior office door access is controlled by the tenant company.
People new to access control may think the system is made up only of the card and the card reader mounted on the wall next to the door. There are a few more parts behind the scenes, all working together to make the magic of granting access to the right person. That’s what this guide is about. Reading it will give you a full and comprehensive understanding of how access control systems work and the language required to communicate with vendors.
Is it absolutely necessary that you learn about access control yourself? No, definitely not. But it will save you time if, in the middle of your project, a problem arises or an important choice must be made. You can seek advice from the installers but they’ll likely answer in access control language; however, you don’t have to take a crash course or call a security-control consultant just yet. But when you do, it helps to have a basic grasp on the subject and your education is free when an online search turns up a resource like this.
How Access control system is used?
Access control system are connected their servers using multiple technologies which includes Cloud servers, Wired network, wireless network and IOT based system.
LAN and Optical Fiber technology
Mobile and Smartphone-based access control system
IOT-based access control system
Cloud-Based Access Control:
In the access control technology, the access permissions are not stored on a local server, but in the cloud. This means that the administrator can manage the permissions from home, or while on vacation anywhere, simply by using a browser. This appeals to security managers charged with overseeing multi-location facilities. It can be done using Emails, online softwares.
Mobile or Smartphone based system:
Mobile or smartphone access control works on the same principle as mobile accessed email, once an app has been downloaded, users are able to access and respond to their mail as long as they enter the correct sign-in credentials. The same is true for smartphone-based access control. Once authorized, and users have downloaded the access control app to their smartphones, they’re able to do the same thing; namely, sign in with their user account, and as soon as their authorized keys appear, select which door to open. The difference with Kisi, for instance, is that they just hold their phone to a Bluetooth or Near Field Communications (NFC) reader, and the door will unlock, but the permissions (log-in credentials) are checked in the background, just like sending an email.
IOT based access control system:
Wired technology: It is the most trusted technology by the users and integrators as it is not dependent any third party and it creates its own network. Access control lock, readers are connected with the server using the Lan wire or the optical fibers. Even though it’s a wired network but it has got no limitation related to the access of the servers from a remote site. It is also trusted as when the system works on Intranet then it keeps the system safe from the cyber threats and intrusions.
Explanation of how it works?
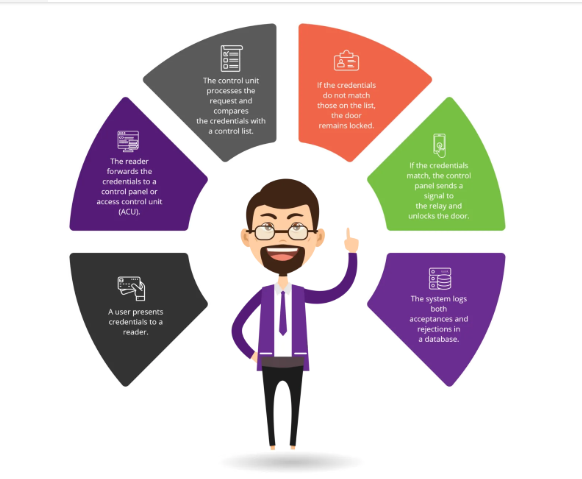
- AUTHORIZATION – Authorization is the phase that turns strangers into members. The first step is to define company policy; determine what people can and cannot do. This should include who has access to which door(s), and whether members of the organization can share access.
- AUTHENTICAION – Authentication goes one level deeper than authorization. In this phase, members present to a door reader whatever badge, token, or credential they were given upon being authorized. The reader will check its validation to determine whether or not it should unlock the electric lock on the door in question.
- ACCESS – Now that the credentials have been authenticated, the access tools available at this stage make sure everyone gets in the right door, at the right time, faster and easier.
- MANANGE – This phase helps the administrator meet several challenges, including adding new access points, onboarding and offboarding users, maintaining security, and troubleshooting problems. Let’s examine some advantages.
- AUDIT – Auditing physical access control is useful for all types of businesses. In addition, it helps certain sectors meet special requirements.
Access Control Technologies
FLAPBARRIER

ROAD BLOCKER

BOLLARD
DOOR ACCESS CONTROL
UVSS
BOOM BARRIER

TYRE KILLERS
TURNSTILE
Door Access Control :
A door access control system determines who is allowed to enter or exit, where they are allowed to exit or enter, and when they are allowed to enter or exit. This was partially done through readers, keys and locks. Only authorised people are allowed to come inside the premises.
The term access control often brings images of access controlled doors, vaults, secure elevators, buildings and secret places. However, today’s access control also includes rooms, workstations, file cabinets, desk drawers, along with equipment like printers or computers.
A typical system has two major components: One controlling the access to a physical location and a system verifying the presence of authorized personnel. The electronic access controlling the physical location, such as a door, typically contains several elements: The lock, the reader, a control panel to authenticate the credentials, along with access control hardware and software.



CRASH RATED SECURITY BOLLARDS:
The rising bollard comes with a push-button hold to run control as standard.
The bollard system can be customised to interface with a wide range of access control equipment to suit specific customer requirements. Available configurations include (but are not limited to) inductive loop systems, card readers, communication equipment and manned guard emergency systems.
Customed Designed and manufactured by engineers with significant experience in the fields of high security and access control, bollards are installed at the perimeter to prevent any forceful intrusion in the perimeter by intruders and terrorists.
Crash Bollards which has been physically tested in HORIBA MIRA, UK according to new IWA 14:2013 std. Our bollards have been impact tested with a 7.2ton truck @ 48kmph (K4) and 7.2ton truck@ 80kmph(K12).
This is a specialist high security product and is designed for use with vehicles only and a full site risk assessment must be carried out at design stage to ensure that all relevant safety systems are included. Where the bollard control point is remote from the installation, we strongly recommend the integration of the system with recordable CCTV system, access control system and BMS systems. For safety reasons pedestrians, cyclists and motorcycles should not to use a bollard controlled roadway.
How Bollard works?
Bollards are used as a first line of deterrence for forceful intrusion by vehicles in to the premises. As the name suggests it crash the vehicle in order to stop the forceful entry and exit from the premises with out authority. It also helps in blocking the road permanently. It helps Security officers or owners of the premises to control the movement of vehicles or restrict the movement of vehicles. Bollards can also be integrated with the CCTV Surveillance system, access control system available at the site, Building management software and the Command and control centre to operate and control all the system using a same portal.
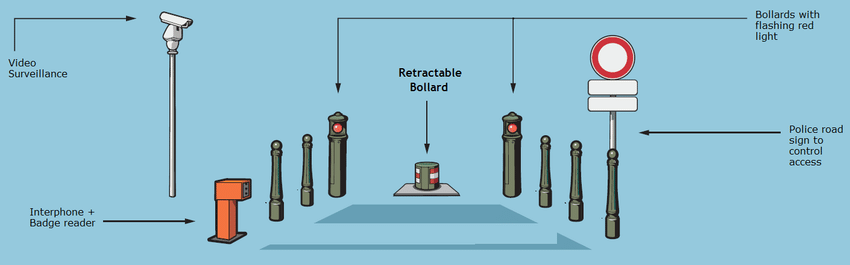
Applications:
- Defence Sites
- Government Buildings
- Prisons
- Airports
- Marine Ports and Shipyards
- Nuclear Power Station and Oil Refineries
- Industries
- School and Universities
- Residential Areas
- Parking Lots
Preferred Brands:
Boom Barrier:
Automatic boom barrier offers security at the exit and the entry points of Defence Areas, Government Building and premises, industrial unit, offices, corporate houses, residential areas, parking lots, toll tax plazas etc. Automatic barrier can be used to successfully control pedestrian and vehicle traffic. It can be used achieve better security and access control on the vehicles and human. High performance Boom Barriers offered by Green IP ™ are suitable for any type of installation atmosphere and terrain. The wide range of lengths and accessories available ensures that all installation requirements and client requirements are met. All models are equipped with a facility of manual operation in the event of power failure and battery back-up capability in selected models. Boom Barriers are also integrated with the CCTV surveillance system, Access control long range readers, Visitor management system, vehicle management system and Building Management system.
How Boom Barrier works?
Boom barrier is installed on the Entry and Exit gate, access permit of vehicles and humans are controlled by Boom barrier. Boom barrier is monitored, controlled and operated either manually or automatically. It is either controlled by humans or machines. Boom barrier is integrated with the Access control readers/antennas and it reads data from the RFID installed at the wind screen of Car or ID of a visitor then the data is sent back to Server for verification and authentication and then the decision is taken regarding the permit inside the premises or not.
Boom barrier can also be integrated with the third party systems like CCTV surveillance system, access control system and Building Management System.
Applications:
1- Defence Sites
2- Government Buildings
3- Airports
4- Marine Ports and Shipyards
5- Nuclear Power Station and Oil Refineries
6- Industries
7- School and Universities
8- Residential Areas
9- Parking Lots
10- Toll Collection centres
Tyre Killers:
Tyre Killer is an electro hydraulically operated heavy duty spike barrier which rises above the ground level on giving a valid input signal and thus prevents unauthorized intrusions at entry/exit points of high security premises.
When the tyre killer is in a lowered position or un armed the vehicles can pass through, thereby providing a good enhanced security blockage system and when the tyre killer is armed it damages the tyres of the vehicle for stopping the vehicle in unathorised entry.
The housing and the blocking element of the Tyre Killer are designed in full core steel profile construction with heavy coating, ensuring maximum safety against corrosion. The impact face of the Tyre Killer is impact resisting thick, sharp steel spikes to puncture the tyre and in fact are strong enough to break the axle of the vehicle. It transfers mechanical forces to reinforced concrete
How Tyre Killer works?
The tyre killer is operated by high speed hydraulic cylinders. A power pack containing an electric motor – pump assembly and an accumulator/handle for manual operation(in case of power failure) is installed up to a distance of 20 meters from the tyre killer in an all weatherproof lockable steel casing on a concrete base. The operation time for up & down movement of the tyre killer varies from 2-6 seconds. It can either work as a standalone system or it can be operated through the Electronics system and server. It can be integrated with the CCTV system, access control and Command Control System for remote control and operation. It is used to stop the forceful entry of the vehicle in the premises. Working of the entire system can be explained by the below wire diagram. For any query you can contact us.
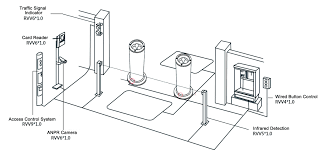
Applications:
1- Defence Sites
2- Government Buildings
3- Airports
4- Marine Ports and Shipyards
5- Nuclear Power Station and Oil Refineries
6- Industries
7- School and Universities
8- Residential Areas
9- Parking Lots
Turnstile:
Turnstile are used to control the access of pedestrians, they can be integrated to operate with access control system such as card readers, providing a secure way of allowing authorised users entry or exit.
Turnstiles can form part of a security fence line, preventing access to unauthorised personnel and secure the perimeter of your premises at the entry and exit of the premises.
They are available in a variety of finishes, including glavanised, painted or in stainless steel etc. It is used for securing pedestrian entrance ways against unauthorised access.
Technology has advanced so much over the past two decades, meaning that turnstiles are smarter and more reliable than ever. They can control the flow of traffic in certain areas, providing a consistent stream of traffic at a controlled rate.
Nowadays, turnstiles can be programmed to limit access – for example, staff can access certain areas whereas visitors cannot. They provide a physical deterrent, limiting those who wish to access an area without authority
How Turnstile works?
Turnstile is a physical barrier on the entry and exit for the pedestrians for their permit to the site. Turnstile is a form of an access control which is used to allow access to the authorized person in the premises. As the technology has advanced, turnstile can either work as a standalone system or it can be integrated with other systems like Cctv Surveillance system, access control, visitor management system, vehicle management system, lift system and Command and control system etc.
As soon as a visitor comes and put the Access card, Biometric scan, RFID Card or the Retina in front of the reader/scanner, it sends the data back to the server for authentication and if the person is allowed to enter, it will rotate the turnstile and allow the person or else it will trigger the person to alert the security person for breach of security. It can also be intregrated with the cctv surveillance system for better surveillance of the premises and it can also be integrated with the Access control system which can be used to access the building/premises/lift etc. Working of the turnstile can be easily understood from the below diagram.

Applications:
- Defence Areas
- Government Buildings
- Airports
- Malls
- Public Places
- Railway Stations/Metro Stations
- Industries
- School and Universities
- Parking Lots
Flap Barrier:
Automatic Flap barrier gates, you will find these gates on the office entrances, airports, stations and also in other many places. Flap barrier gates provided with a device for emergency control. This allows an automatic opening for two wings while people walk through the gate with the access cards. After that, it closes down in a minute. The flap barrier is composed of a chassis, core component, wing arms, Printed Circuit Board (PCB), infrared sensors, reader, and access control system. The system uses standard electric interfaces. It meets fire-fighting passage requirements and is equipped with dedicated fire control linkage interfaces. The entire system complies with the same quality standard to ensure reliability, stability, and smoothness of the system during operation.
How Flap Barrier works?
Flap Barrier gates have a simple working principle. Flap barriers manage the crowd on the industrial places like Exhibitions, supermarkets, metro, and public transports. It is utilized mostly for Business and industrial places. The Method of an Automated Security Gate or Flap Barrier varies in Size, Shape, and Performance. Flap barriers are works with illuminated wings that can move or control by bi-directional movement. Flap Barrier gates provided with a sensor to the prevention purpose. The mechanism provides the feature to the gate wings can automatically open and hide. RS232 serial communication port is used to control the opening of the barrier After the signal received by the card access, the system automatically closes the flap barrier after few seconds. Flap barrier provided with an Anti-pinch function which protects a person against injury caused by the closing of wing arms at the end of the preset pass-through duration.
After powered on, the flap barrier main board performs self-test to check whether the hardware works normally. If any failure is detected, the system will display a text prompt on the LCD screen. The user can quickly solve the problem based on these prompts. After the reader receives valid user information, the control panel sends barrier opening signals to the flap barrier main board. The flap barrier main board receives, judges and processes the information from the control panel, the infrared correlation tubes and the proximity switch, and then sends commands to the upside indicator light and the electric motor. The upside indicator light turns from red to green and the electric motor is activated to open the flap barrier so that the pedestrian can pass through the channel. This system can also be integrated with the third party systems like CCTV, access control and command & control system.
Applications:
- Inside Offices
- Exhibitions
- Supermarkets
- Railway Stations
- Metro Stations
- Public Transports
- Airports
- Malls
- Schools and Universities
Under Vehicle Surveillance System:
UVSS provides unique facility to scan the hidden area of the Vehicle which cannot be easily monitored or seen by the security officials. Security and surveillance system is complete without the ability to scan the area underneath the millions of vehicles entering and exiting high-risk areas every day.
UVSS is widely used in public establishments such as Sensitive Defence areas, Govt Offices, Public transport areas, malls and large corporate offices buildings with a steady stream of vehicular traffic entering and exiting, operate a most primitive and highly ineffective system of handheld reflective mirrors shoved briefly under a car. Besides being clumsy, it also slows down vehicular movement, causing delays.
Under Vehicle Surveillance System (UVSS) is the perfect solution for such establishments that need to thoroughly check under dozens or hundreds of vehicles every day without slowing down vehicular passage. This system is capable to scan, monitor and digitally record crisp, clear digital video and images of the entire width of a vehicle’s underside. Our surveillance cameras which are enabled with the Artificial inteilligence system detects the foreign objects and threats to help you to mitigate risks. UVSS is a fully automated system that does instantaneous inspection of vehicle undercarriage using digital line and area scanning technologies, and triggers an alarm if its scan detects doubtful elements, including explosive devices.
It can be fixed permanently into the ground to inspect vehicles passing above, or it can be mounted on a mobile unit to be used manually or robotically at flexible locations.
How UVSS works?
The Under Vehicle Surveillance System works with Automatic Number Plate Detection camera and High resolution cameras which gives security officials a clear, sharp images of the vehicles undercarriage. It also uses the Bright white, high-intensity LED-based lighting illuminates the vehicle’s undercarriage so details are not lost in shadows and the hidden objects are easily seen through the camera. It uses color area scanning technology to effectively scan and inspect the undercarriage of vehicles to search and analyze images for explosive devices, suspicious objects or contraband such as drugs and weapons. And with the ability to place cameras anywhere along the length of the ramp, wheel wells and other details are easy to capture. Focal length, field of view, and angle of the camera simulate a person in a pit viewing vehicles passing over. The video is then transmitted to the Server for deep analysis using the artificial intelligence and then the software can easily trigger the alarm in case of any hidden object found.
For better results, UVSS system in installed with either Bollard and boom barrier system at the entry and exit of the premises. UVSS is also used with ANPR and Visitor management system. As soon as the vehicle comes to the entry point, ANPR reads the Vehicle no and informs the security official regarding the same and the vehicle no is sent to the server for its authorization and if the vehicle is authorized to entry then the Boom barrier will automatically open and the vehicle will pass over the UVSS and the security official will see the undercarriage photo and video of the vehicle, in case of no suspicion and no foreign object the vehicle will be allowed to come in the premises. It can be easily understood from the below diagram.



Applications:
- Defence
- Government
- Transporation
- Public Places
- Malls
- Airports
- Corporate Offices
Road Blocker:
Road Blocker is an electro hydraulically operated heavy duty iron machine rising step obstruction which rises above the ground level on giving a valid input signal and thus prevents unauthorized intrusions at entry/exit points of high security premises. When in lowered position the vehicles can pass through and thereby providing a good enhanced security blockage system to the perimeter and deterrence to the forceful entry. The housing and the blocking element of the Road Blocker are designed in full core steel and heavy duty iron and construction with heavy coating for rust proof properties,ensuring maximum safety against corrosion. The impact face of these road barrier is reinforced with steel ribs and impact plates to transfer mechanical forces to reinforced concrete foundation.

How Road Blocker works?
Road blocker is used as a barrier to the unauthorized forceful entry in the premises by the vehicle. It can not only stops the vehicle instead it will damage the vehicle that it can’t enter the premises. The road blocker is operated by high speed hydraulic cylinders. A power pack containing an electric motor, casing and pump assembly and an accumulator/handle which are used in manual operation (in case of power failure) is installed upto a some distance from the road barrier in an all weatherproof lockable steel casing on a concrete base. Road blocker technology has been advanced and it can either work as a standalone system on the site or it can be integrated with the security and surveillance system available on the customers site like CCTV surveillance system, access control system, bollard system, boom barrier system etc.
Applications:
- Sensitive Defence Sites
- VVIP Residential sites
- Government sites
- Airports
- Naval Ports
- Prisons
- Ammunition depots
